1.2. Linux Basics #
Introduction #
An operating system provides a way to interact with the hardware components of the computer, and provides an execution environment for applications.
The following functions are providing by an OS:
- CPU Management
- Memory Management
- Device Drives
- IO Management
- Applications
Linux Base File System #
The Linux filesystem is structured in accordance to the Filesystem Hierarchy Standard.
| Path | Description |
|---|---|
/sbin | Binaries needed for administration (sudo binaries) |
/bin | All system binaries |
/boot | Files required for booting (e.g. Linux kernel and system.map) |
/dev | All devices |
/etc | Configuration files |
/home | User home directories |
/lib | Shared libraries (.so files) (DLLs in Windows or dylibs in macOS) |
/mnt or /media | User mounted filesystems |
/opt | Additional add-on packages |
/root | Home directory for root (admin) user |
/usr | Shareable read-only directory |
/var | Log files, MySQL/database files, web server data files, email inboxes, etc. |
File Permissions #
File permissions in Linux specify the access allowed at owner, group, and global level, plus some additional special attributes.
A typical permission, in string form, could look something like this: -rw-r--r--. This shows that:
- It is not a directory (otherwise first
-would bed) - The owner (user) has read-write access to the file
- The group the owner is in has read access
- Everyone (other) else has read access
| Special Attributes | User | Group | Other | ||||||
|---|---|---|---|---|---|---|---|---|---|
| d | r | w | x | r | w | x | r | w | x |
| - | r | w | - | r | - | - | r | - | - |
x means Execute permission, which allows that scope to run executable scripts.
Octal Permissions #
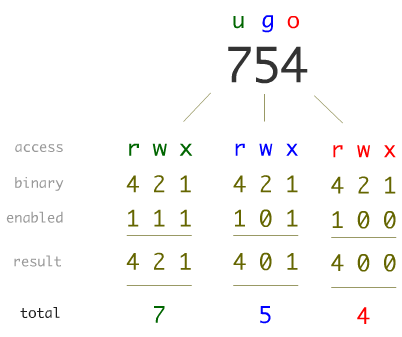
When using commands in Linux, you will notice that internally permissions are stored as a 3 or 4 digit number. This is the permission in octal form.
For example:
644would be-rw-r--r--(same as above)777would berwxrwxrwx000would be---------
Generally the larger each digit the more open the permissions are.
To calculate the octal permission, for each scope (user, group, global), write the binary of each permission, then take the value of the resultant number (as shown in the image below).
Special Permissions #
d: Directory (d---------)s: SUID or SGID depending on usage:rws------: SUID, the file will always execute as the user that owns the file, no matter what user executes it.---rws---: SGID, the file will always execute as the group that owns the file.
t: Sticky bit (d------rwt), allows only the owner of the directory to delete files within it.
Logs #
Linux stores logs of just about everything that happens on the system. This is useful for solving issues, and also forensics.
Logs are stored in the /var/log directory.
Common log files:
auth.logorsecure: shows login eventsapt/history.logoryum.log: shows package manager eventssyslogormessages: shows kernel messages
Time #
Time in Linux is stored as a Unix timestamp. This is the number of seconds passed since 1st January 1970.
File access, modification, and creation times can easily be changed in Linux, which can make forensics more difficult.